38 security labels are used in what type of model
OSI Security Layers and Their Significance - W3schools The first three layers of the OSI model are called the media layers. Physical Layer is used for defining the technical qualifications of the data connectivity. Since the security in this layer is critical, so in case of any cyber danger (DoS attack), it is recommended to unplug the cable from the primary system. Access Control using Security Labels & Security Clearance - Isode Security labels are widely used as a mechanism for controlling information access, for a number of reasons. The model of security labels and clearances is very easy to understand. This is important, as complex models are more prone to user error.
Classifying Data | CISSP Security Management and Practices | Pearson IT ... The classifications for the sensitivity of data used in government and military applications are top secret, secret, confidential, sensitive but unclassified, and unclassified. The implementation of the classification is based on laws, policies, and executive directives that can be in conflict with each other.

Security labels are used in what type of model
Security by Labeling | September 2022 | Communications of the ACM Simple yet effective labels convey relevant cybersecurity information to buyers at the point of sale and encourage IoT vendors to up their cybersecurity game as they now can recoup their security investments from risk-aware buyers. These dynamics benefit consumers and the industry alike, resulting in better, more resilient cybersecurity for all ... Security printing - Wikipedia Security printing is the field of the printing industry that deals with the printing of items such as banknotes, cheques, passports, tamper-evident labels, security tapes, product authentication, stock certificates, postage stamps and identity cards. The main goal of security printing is to prevent forgery, tampering, or counterfeiting. Evaluate Model: Component Reference - Azure Machine Learning 10.11.2021 · Use this component to measure the accuracy of a trained model. You provide a dataset containing scores generated from a model, and the Evaluate Model component computes a set of industry-standard evaluation metrics. The metrics returned by Evaluate Model depend on the type of model that you are evaluating: Classification Models; Regression Models
Security labels are used in what type of model. Chapter 4. Introduction to Access Controls Flashcards | Quizlet Which of the following are part of a security label used in the mandatory access control model? (Select all that apply.) a. Classification b. Category c. Role d. Location A and B. Classification and category are typically found in a security label. 12. Which access control model uses the function of a subject in an organization? a. cloud.google.com › security-command-center › docsVulnerabilities findings | Security Command Center - Google Cloud Sep 06, 2022 · The following tables describe Security Health Analytics detectors, the assets and compliance standards they support, the settings they use for scans, and the finding types they generate. You can filter findings by detector name and finding type using the Security Command Center Vulnerabilities tab in the Google Cloud console. PDF Information Security CS 526 •A security policy -defines the security requirements for a given system •Verification techniques that can be used to show that a policy is satisfied by a system •System Model + Security Policy = Security Model CS526 Topic 17: BLP 9 Approach of BLP •Use state-transition systems to describe computer systems valohai.com › model-deploymentWhat is Model Deployment - Valohai Model deployment is simply the engineering task of exposing an ML model to real use. The term is often used quite synonymously with making a model available via real-time APIs. Still, we should think about model deployment more broadly – as online inference in the cloud isn’t always a necessary or even a desirable solution.
Security Labels, Stickers & Seals Anti Tamper - NovaVision Security labels and stickers provide an anti-tamper seal for file cabinets, doors, windows, equipment, boxes, and many other containers. All of our security labels have pressure-sensitive adhesive -- just peel and stick. Protect Your Products and Equipment Control Access to Files, Doors, & Containers Indicates Tampering or Pilfering Mandatory access control - Wikipedia In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system or database constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/UDP ... Introduction To Classic Security Models - GeeksforGeeks These models are used for maintaining goals of security, i.e. Confidentiality, Integrity, and Availability. In simple words, it deals with CIA Triad maintenance. There are 3 main types of Classic Security Models. Bell-LaPadula Biba Clarke Wilson Security Model 1. Bell-LaPadula RFC 6797: HTTP Strict Transport Security (HSTS) - RFC Editor RFC 6797 HTTP Strict Transport Security (HSTS) November 2012 Readers may wish to refer to Section 2 of [] for details as well as relevant citations. 2.3.1.Threats Addressed 2.3.1.1.Passive Network Attackers When a user browses the web on a local wireless network (e.g., an 802.11-based wireless local area network) a nearby attacker can possibly eavesdrop on the user's …
Overview of Cloud Native Security | Kubernetes 3.9.2022 · Each layer of the Cloud Native security model builds upon the next outermost layer. The Code layer benefits from strong base (Cloud, Cluster, Container) security layers. You cannot safeguard against poor security standards in the base … How to use Microsoft Info Protection (MIP) sensitivity labels- ShareGate Enable sensitivity labels for Office files in SharePoint and OneDrive. * Automatically apply sensitivity labels to documents and emails. Configure Microsoft 365 sensitivity labels at the Files & emails scope. Apply a sensitivity label to content automatically. * Use sensitivity labels to protect content in Microsoft Teams and SharePoint. Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access. (Solved) - Question 1.) There are many types of security models are ... The model is a formal state ...
Learn about sensitivity labels - Microsoft Purview (compliance) For example, under Confidential, your organization might use several different labels for specific types of that classification. In this example, the parent label Confidential is simply a text label with no protection settings, and because it has sublabels, it can't be applied to content.
Why do we have four levels of security in Power BI? Row-Level-Security (RLS) controls who has access to which data in the data model. This feature of Power BI is well documented and understood in the community. There are three forms of this feature: Lookup-Tables with E-Mail addresses Parent-Child Relationships Dynamic RLS
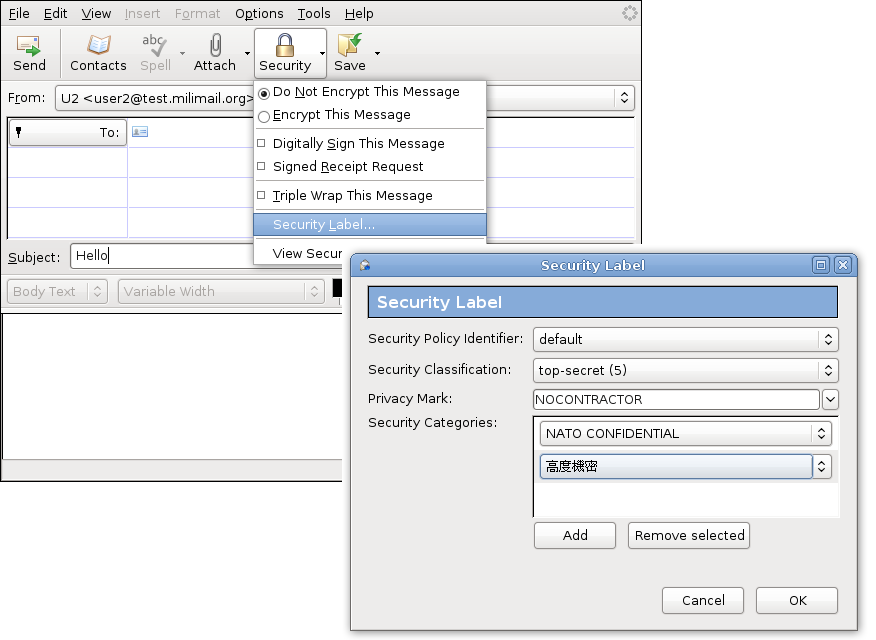
4.3 SECURITY MECHANISMS | Internet & Intranet Security The general concept of trusted functionality can be used to either extend the scope or to establish the effectiveness of other security mechanisms. Any functionality that directly provides, or provides access to, security mechanisms should be trustworthy. System resources may have security labels associated with them, for example, to indicate sensitivity levels.
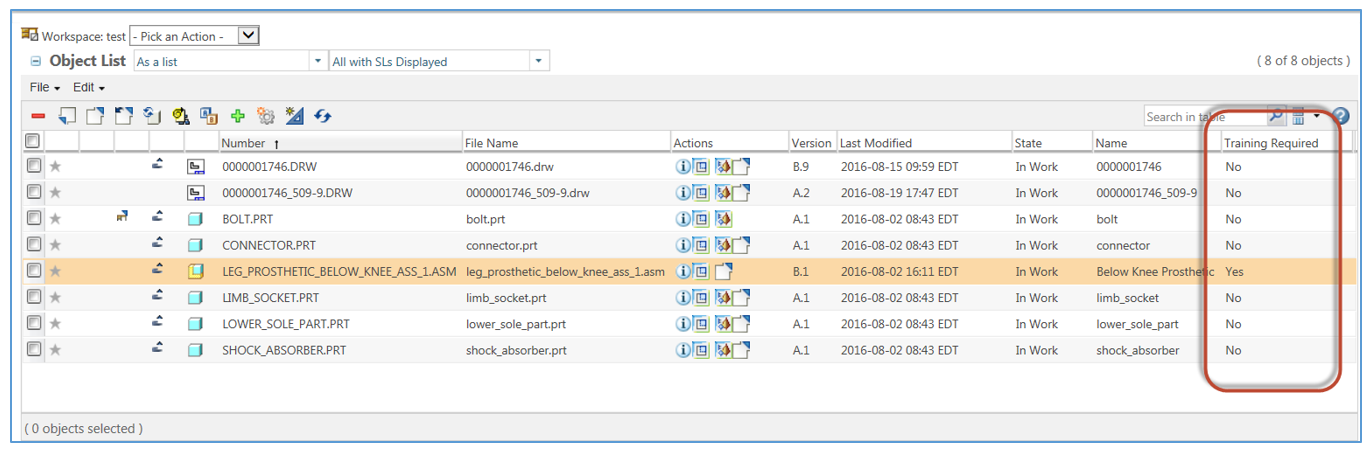
Access Control Models - UHWO Cyber Security - University of Hawai'i ... MAC uses "security labels" to assign resource objects on a system. There are two pieces of information connected to these security labels: classification (high, medium, low) and category (specific department or project - provides "need to know"). Each user account is also assigned classification and category properties.
Amazon.com: Uniclife 28-Key Steel Key Cabinet with Combination … Secure Construction: 8" L x 3" W x 9.8" H. Made of 0.8 mm heavy-duty frosted steel sheet for optimal security. And the solid piano hinge makes it unlikely to be pried open to avoid forced entry. 28 Tags in 5 Colors: Contain 28 larger but light key tags with labels to write and clear windows for easy visibility.
docs.microsoft.com › whitepaper-powerbi-securityPower BI security white paper - Power BI | Microsoft Docs Jul 10, 2022 · Row Level security with Power BI can be used to restrict data access for given users. Filters restrict data access at the row level, and you can define filters within role. Object-level security (OLS) can be used to secure sensitive tables or columns. However, unlike row-level security, object-level security also secures object names and metadata.
Security Containers | GSA All GSA-approved containers must have a GSA approval label, or a GSA recertification label on the front of the equipment in order to store classified National Security Information (NSI) or weapons. The Information Security Oversight Office (ISOO) issued a notice requiring federal agencies to purchase GSA Approved containers using National Stock ...
What is Model Deployment - Valohai Model deployment is simply the engineering task of exposing an ML model to real use. The term is often used quite synonymously with making a model available via real-time APIs. Still, we should think about model deployment more broadly – as online inference in the cloud isn’t always a necessary or even a desirable solution.
Security Chapter 2 Flashcards | Quizlet This model uses labels (or attributes) for both subjects and objects. Any operation by any subject on any object will be tested against a set of authorization rules (or policies) to determine if the operation is allowed. Discretionary Access Control (DAC)
Different Type of Security Tags | Retail Security | SecurityTags.com There are two widely used types of locking mechanisms available; magnetic and mechanical, with magnetic tags available in a series of strengths ranging from standard to SuperLock, HyperLock and Multi-polar. The stronger the magnetic lock, the harder the tag is to illegally remove, which is why a minimum strength of SuperLock is recommended.
cloud.google.com › docs › creating-managing-labelsCreating and managing labels | Resource ... - Google Cloud Sep 06, 2022 · Team or cost center labels: Add labels based on team or cost center to distinguish resources owned by different teams (for example, team:research and team:analytics). You can use this type of label for cost accounting or budgeting. Component labels: For example, component:redis, component:frontend, component:ingest, and component:dashboard.
Creating and managing labels | Resource Manager … 6.9.2022 · Console. To add labels to a single project: Open the Labels page in the Google Cloud console.. Open the Labels page. Select your project from the Select a project drop-down.. To add a new label entry, click + Add label and enter a label key and value for each label you want to add.. When you're finished adding labels, click Save.. To add labels for more than one project …
Overview of Data Security Unit | Salesforce Trailhead You can balance security and convenience, reduce the risk of stolen or misused data, and still make sure all users can easily get the data they need. The platform makes it easy to specify which users can view, create, edit, or delete any record or field in the app. You can control access to your whole org, a specific object, a specific field ...
Access control: Models and methods in the CISSP exam [updated 2022] CISSP domain 5 covers identity and access management, and objective 5.4 within that domain is "Implement and manage authorization mechanisms.". There are six main types of access control models all CISSP holders should understand: Mandatory Access Control (MAC) Discretionary Access Control (DAC) Role-Based Access Control (RBAC) Rule-Based ...
ITIL security management - Wikipedia ITIL security management describes the structured fitting of security into an organization.ITIL security management is based on the ISO 27001 standard. "ISO/IEC 27001:2005 covers all types of organizations (e.g. commercial enterprises, government agencies, not-for profit organizations). ISO/IEC 27001:2005 specifies the requirements for establishing, implementing, …
Sensitivity labels from Microsoft Purview Information Protection in ... Sensitivity labels are retained when you move your content back and forth between Desktop and the service in the form of .pbix files. In the Power BI service, sensitivity labels can be applied to datasets, reports, dashboards, and dataflows.
IoT Sec 1.1 Fundamentals: IoT Security Final Exam Answers This work role conducts comprehensive assessments of the management, operational, and technical security controls to determine their overall effectiveness. 6. Put the steps in the Threat Modeling process into the correct order. (Not all options are used.) IoT Security (Version 1.0) - IoT Fundamentals: IoT Security Final Exam 38 7.
docs.microsoft.com › evaluate-modelEvaluate Model: Component Reference - Azure Machine Learning Nov 10, 2021 · Use this component to measure the accuracy of a trained model. You provide a dataset containing scores generated from a model, and the Evaluate Model component computes a set of industry-standard evaluation metrics. The metrics returned by Evaluate Model depend on the type of model that you are evaluating: Classification Models; Regression Models
Security Models | CISSP Exam Cram: Security Architecture and Models ... The Information Flow model consists of objects, state transitions, and lattice (flow policy) states. The real goal of the information flow model is to prevent unauthorized, insecure information flow in any direction. This model and others can make use of guards. Guards allow the exchange of data between various systems. Noninterference Model
en.wikipedia.org › wiki › ITIL_security_managementITIL security management - Wikipedia Internal e-mail is subject to multiple security risks, requiring corresponding security plan and policies. In this example the ITIL security Management approach is used to implement e-mail policies. The Security management team is formed and process guidelines are formulated and communicated to all employees and providers.
Types of Security Mechanism - GeeksforGeeks Bit stuffing : This security mechanism is used to add some extra bits into data which is being transmitted. It helps data to be checked at the receiving end and is achieved by Even parity or Odd Parity. Digital Signature : This security mechanism is achieved by adding digital data that is not visible to eyes. It is form of electronic signature ...
Comparing Labels and Lattice - Get Certified Get Ahead The mandatory access control (MAC) model uses labels (sometimes referred to as sensitivity labels or security labels) to determine access. Security administrators assign labels to both subjects (users) and objects (files or folders). When the labels match, the system can grant a subject access to an object.
Which type of access control model assigns security level labels to ... attribute-based Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications.
Amazon.com: AVERY 5267 Easy Peel Return Address Labels, Laser… The labels adhere strongly to everything I have used them on (regular paper, gloss, envelopes of all sorts). We use an HP LaserJet MFP M180nw and have had absolutely no problems with feeding at all, but you do need to make sure you're changing the 'paper type' setting before printing as this can cause issues otherwise.

100 Total Transfer Tamper Evident Security Warranty Void Stickers/ Labels/ Seals (Red, 30x90 mm, Serial Numbers - TamperSTOP)
› Avery-Address-Printers-PermanentAmazon.com: AVERY 5267 Easy Peel Return Address Labels, Laser ... Make sure this fits by entering your model number.; Guaranteed to stick and stay: Avery labels with Ultrahold permanent adhesive hold fast to envelopes, cardboard, paper, plastic, glass, tin and metal; great for bulk mailing, filing, organization, product packaging and gifting
Evaluate Model: Component Reference - Azure Machine Learning 10.11.2021 · Use this component to measure the accuracy of a trained model. You provide a dataset containing scores generated from a model, and the Evaluate Model component computes a set of industry-standard evaluation metrics. The metrics returned by Evaluate Model depend on the type of model that you are evaluating: Classification Models; Regression Models
Security printing - Wikipedia Security printing is the field of the printing industry that deals with the printing of items such as banknotes, cheques, passports, tamper-evident labels, security tapes, product authentication, stock certificates, postage stamps and identity cards. The main goal of security printing is to prevent forgery, tampering, or counterfeiting.

50-Pack 100% Total Transfer Tamper Evident Security Warranty Void Stickers/ Labels/ Seals (Red, Large 35 x 120 mm, Triple Serial Numbers - TamperSTOP)
Security by Labeling | September 2022 | Communications of the ACM Simple yet effective labels convey relevant cybersecurity information to buyers at the point of sale and encourage IoT vendors to up their cybersecurity game as they now can recoup their security investments from risk-aware buyers. These dynamics benefit consumers and the industry alike, resulting in better, more resilient cybersecurity for all ...






![PDF] Security model for resource availability - subject and ...](https://d3i71xaburhd42.cloudfront.net/5fa21f5740065e5adbe4ded753ed462033314858/2-Figure1-1.png)
















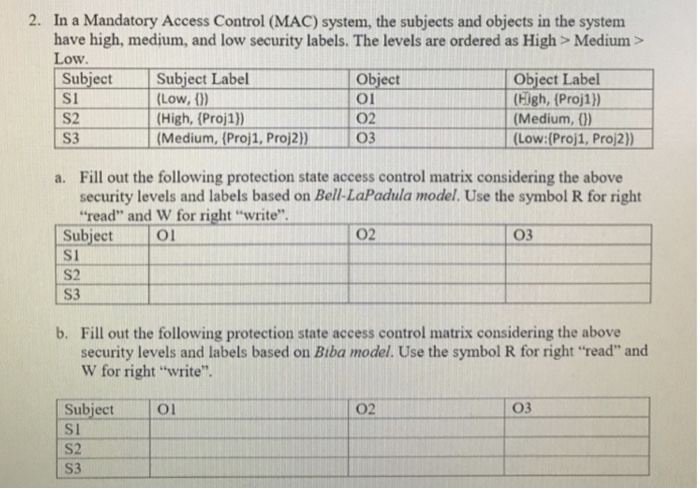




Post a Comment for "38 security labels are used in what type of model"